This was reported 17 months ago to WP, https://core.trac.wordpress.org/ticket/21917
Title: Persistent XSS in Wordpress 3.3.1+dfsg-1 (Packaged with Ubuntu 12.04.4)
Author: Larry W. Cashdollar, @_larry0
Date: 2/1/2014
Vendor: notified won't fix.
Download: http://wordpress.org/download
Versions Impacted: 3.3.1 -> 3.8.1 tested 2/2/2014.
This advisory is a work in progress, updates will be posted here
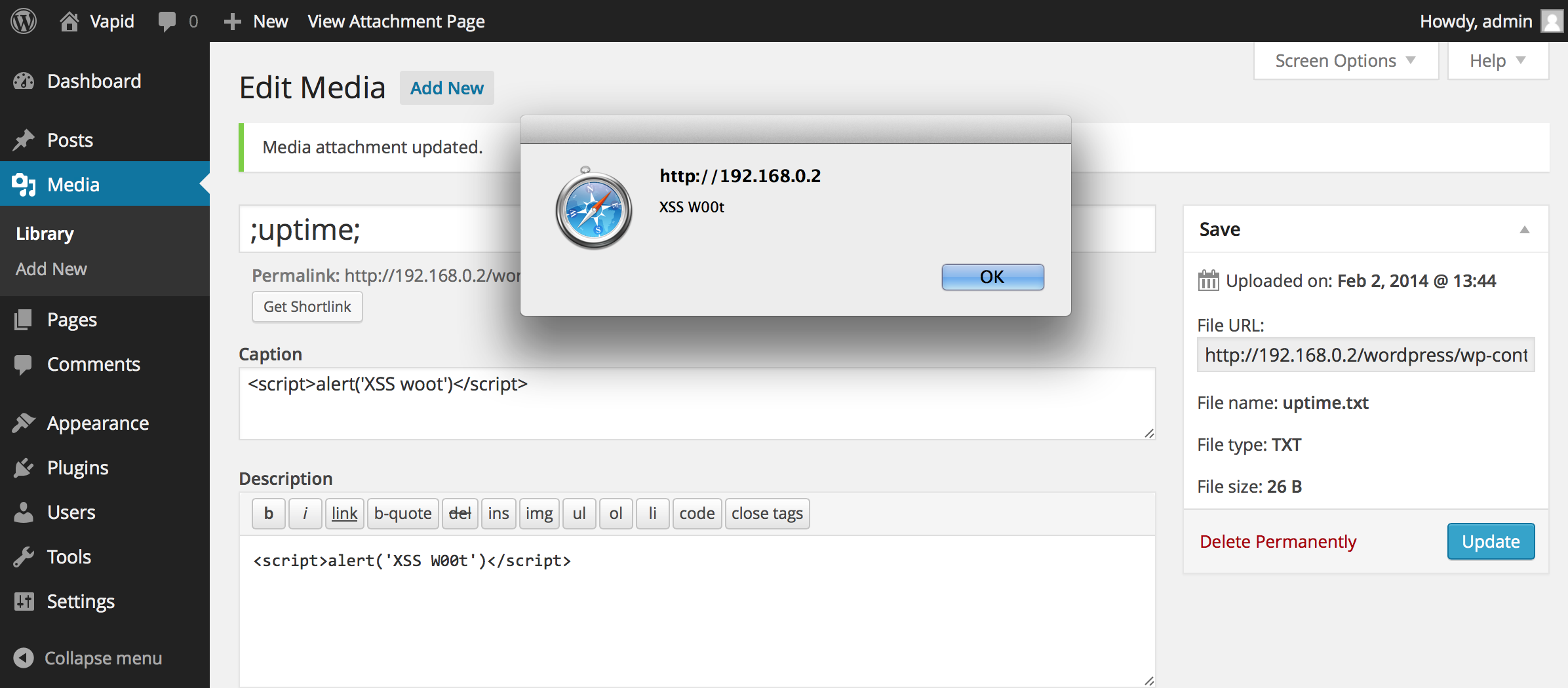
Persistent XSS injection with admin user in description field for Media Library.
Notes:
Line 235 of upload.php renders the 'View' option:
235 <?php $wp_list_table->display(); ?>
Trace wp_list_table->display back to find unsantized html out.
Lines 100-102 of wp-includes/canonical.php call functions to render vulnerable page:
I'll need to investigate further to find vulnerable code once I return from vacation.
100 if ( is_attachment() && !empty($_GET['attachment_id']) && ! $redirect_url ) {
101 if ( $redirect_url = get_attachment_link(get_query_var('attachment_id')) )
102 $redirect['query'] = remove_query_arg('attachment_id', $redirect['query']);
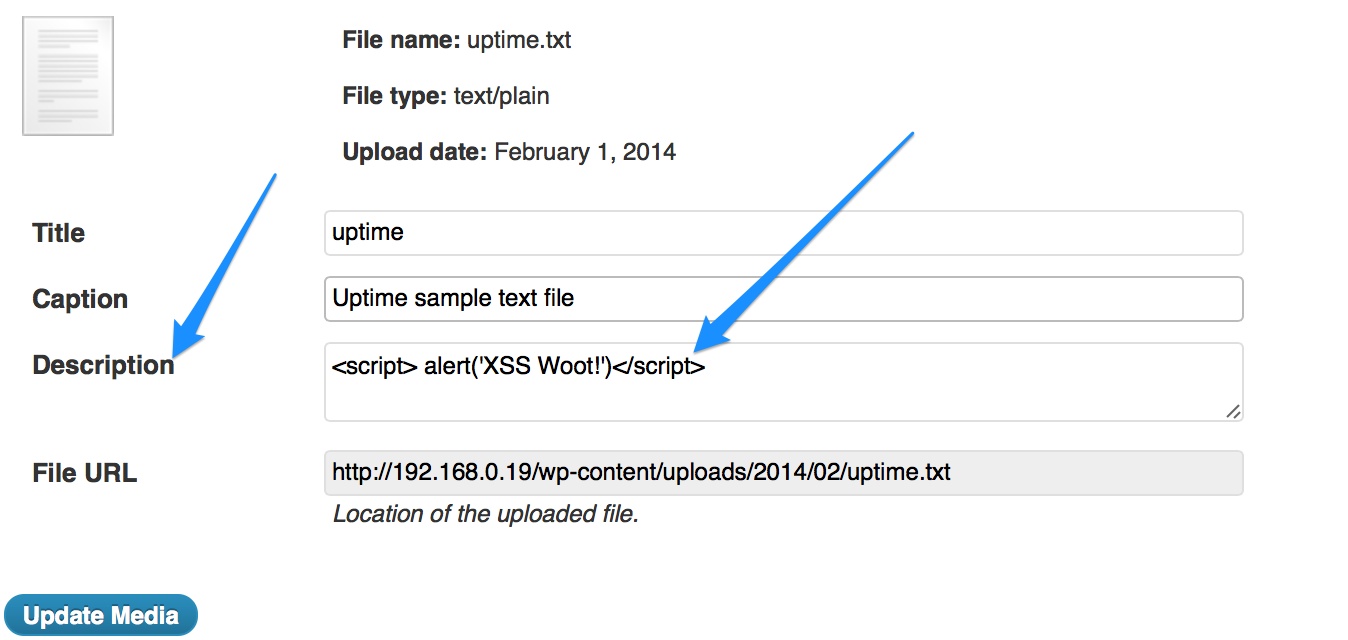
click 'View'

XSS Screen capture
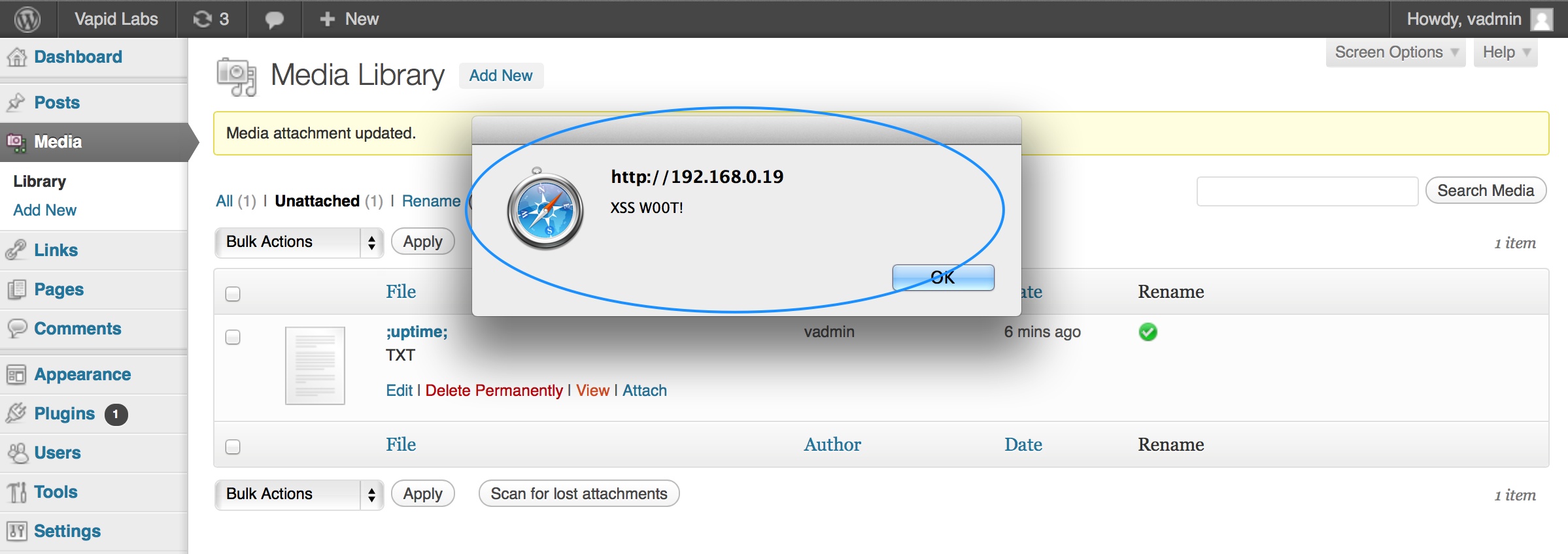
Also tested on wordpress 3.8.1.